Complete Guide to Windows Security & Privacy Protection
Master Windows security with our comprehensive guide. Learn to protect your PC from viruses, malware, and privacy threats with proven techniques.
By Mike Torres
After 10+ years in cybersecurity—from consulting with businesses to helping everyday users—I’ve learned one critical lesson: good security doesn’t have to be complicated. It just has to be consistent.
Here’s the thing most security advice gets wrong: it’s either so paranoid nobody follows it, or so relaxed it leaves you vulnerable. The reality? You need practical security that actually fits into your daily life.
In this comprehensive guide, I’ll walk you through everything you need to protect your Windows 11 PC from the threats you’ll actually face in 2025. No fear-mongering, no selling you unnecessary software—just the straight truth about what works.
Understanding the Modern Threat Landscape
Let me be honest about what you’re really up against. The threats facing Windows users in 2025 have evolved significantly from the simple viruses of the past.
Here’s what I see most often in my consulting work:
Ransomware: The Growing Threat
Think of ransomware like a digital hostage situation. Criminals encrypt your files and demand payment for the decryption key. In 2024 alone, I’ve helped a dozen clients recover from ransomware attacks, and here’s what most people don’t realize: the attacks are becoming more targeted and sophisticated.
Modern ransomware often waits weeks before activating, silently corrupting your backups first. That’s why you need a defense-in-depth strategy (more on this later).
Phishing: Still the #1 Attack Vector
I know it seems basic, but phishing is responsible for over 80% of successful breaches I investigate. Here’s why: attackers aren’t trying to hack your computer anymore—they’re tricking you into giving them access voluntarily.
Think of it like someone in a fake UPS uniform showing up at your door. They look legitimate, they sound professional, but they’re actually collecting information to steal your identity. That’s exactly what modern phishing emails do.
Malware and Spyware
The old-school viruses that crashed your system? They’re mostly gone. Modern malware is sneakier—it wants to stay hidden while stealing your data or using your computer for cryptocurrency mining.
Common types I see regularly:
- Info stealers: Harvest passwords, credit cards, browser cookies
- Adware: Injects ads and redirects your searches (annoying but usually not devastating)
- Trojans: Disguised as legitimate software, provide backdoor access
- Cryptominers: Use your PC’s resources to mine cryptocurrency, slowing everything down
Step-by-step malware removal and system cleaning guide
Zero-Day Exploits and Software Vulnerabilities
Here’s the thing about zero-day exploits: you can’t protect yourself with antivirus because the vulnerability is unknown until it’s already being exploited. That’s why keeping Windows and all software updated is non-negotiable.
I’ve seen too many clients get compromised because they disabled Windows Update to “improve performance.” Yes, updates can be annoying. But they patch critical security holes that attackers actively exploit.
Privacy Invasion and Data Collection
Companies—including Microsoft—collect enormous amounts of data about your activities. While not as immediately dangerous as ransomware, this data collection can lead to targeted manipulation, data breaches, government surveillance, and identity theft if databases are compromised. The good news: you can significantly reduce this collection without breaking Windows functionality.
The Defense-in-Depth Strategy
Here’s a security principle I drill into every client: never rely on a single security measure.
Think of it like protecting your home. You don’t just lock the front door and call it secure. You lock windows, maybe install a security system, use outdoor lighting, get to know your neighbors. Each layer provides additional protection, and attackers need to bypass multiple defenses to succeed.
For Windows security, here are your essential layers:
Layer 1: Built-in Security (Microsoft Defender, Firewall) - Your first line of defense, and honestly, better than most people realize. This layer catches most threats automatically if configured correctly, blocking malware, exploits, and unauthorized network access before they reach your data.
Layer 2: Software Updates - Patches vulnerabilities before they can be exploited. Think of updates as locking newly discovered windows and doors in your security perimeter. Attackers actively target unpatched systems because they know exactly where the vulnerabilities are.
Layer 3: Strong Authentication - Prevents unauthorized access even if other defenses fail. If someone steals or guesses your password, strong authentication (2FA, biometrics) ensures they still can’t access your accounts without a second proof of identity.
Layer 4: Safe Behavior - The most important layer, and the one no technical solution can replace. You can have perfect security software, but if you voluntarily give your password to a phisher or download malware disguised as legitimate software, technology can’t save you.
Layer 5: Data Backups - Your safety net when everything else fails. Ransomware encrypted your files? Hardware failed? House fire destroyed your PC? Backups mean you lose nothing but time. Without backups, you’re gambling with irreplaceable data.
The beauty of this approach? Each layer catches what the others miss. Let’s dive into each layer in detail.
Layer 1: Microsoft Defender and Windows Firewall
Let me address the elephant in the room: do you really need third-party antivirus anymore?
For most users, the honest answer is no. Microsoft Defender (they rebranded from Windows Defender back in 2019) has become legitimately effective. I know that contradicts what antivirus companies want you to believe, but I’m here to give you honest advice, not sell software.
Why Microsoft Defender Is Now Sufficient
When Microsoft Defender first launched as Microsoft Security Essentials in 2009, I wouldn’t have recommended it. But Microsoft has invested heavily over the past decade, and current capabilities match or exceed many paid alternatives.
The risk here: Antivirus marketing has convinced many users that Windows Security isn’t “real” protection. That’s simply not true anymore.
What Microsoft Defender provides:
- Real-time malware detection (consistently high rankings in AV-TEST and AV-Comparatives)
- Cloud-delivered protection against emerging threats
- Ransomware protection with controlled folder access
- Exploit protection (guards against zero-day attacks)
- Firewall integration
- Network protection
- Application and browser control
- Device security monitoring
And here’s what people overlook: It’s already integrated into Windows. No performance impact from third-party software, no annoying popups trying to upsell you, no compatibility conflicts.
Setting Up Microsoft Defender Properly
Here’s the thing: Microsoft Defender only works if it’s configured correctly. Let me walk you through the essential settings.
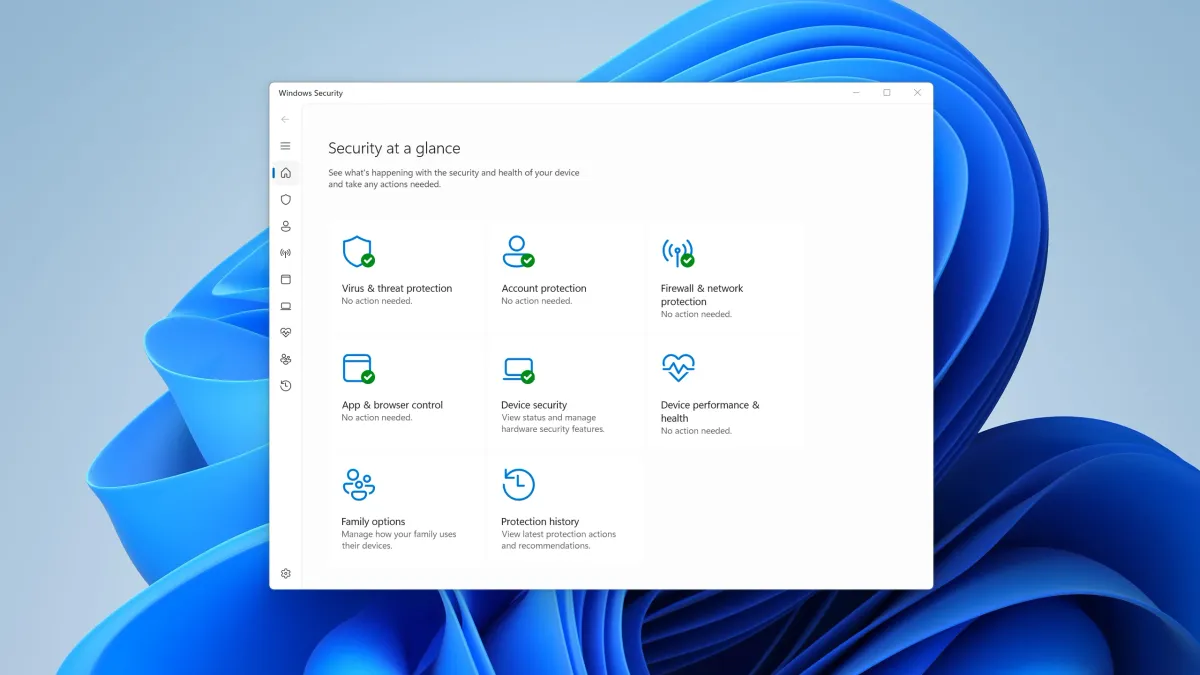
Enable Core Protection (5 minutes):
- Open Windows Security (search for it in Start menu)
- Go to Virus & threat protection
- Click Manage settings under Virus & threat protection settings
- Verify these are enabled:
- Real-time protection - ON (catches threats as they arrive)
- Cloud-delivered protection - ON (uses Microsoft’s cloud intelligence)
- Automatic sample submission - ON (helps identify new threats)
- Tamper Protection - ON (prevents malware from disabling Defender)
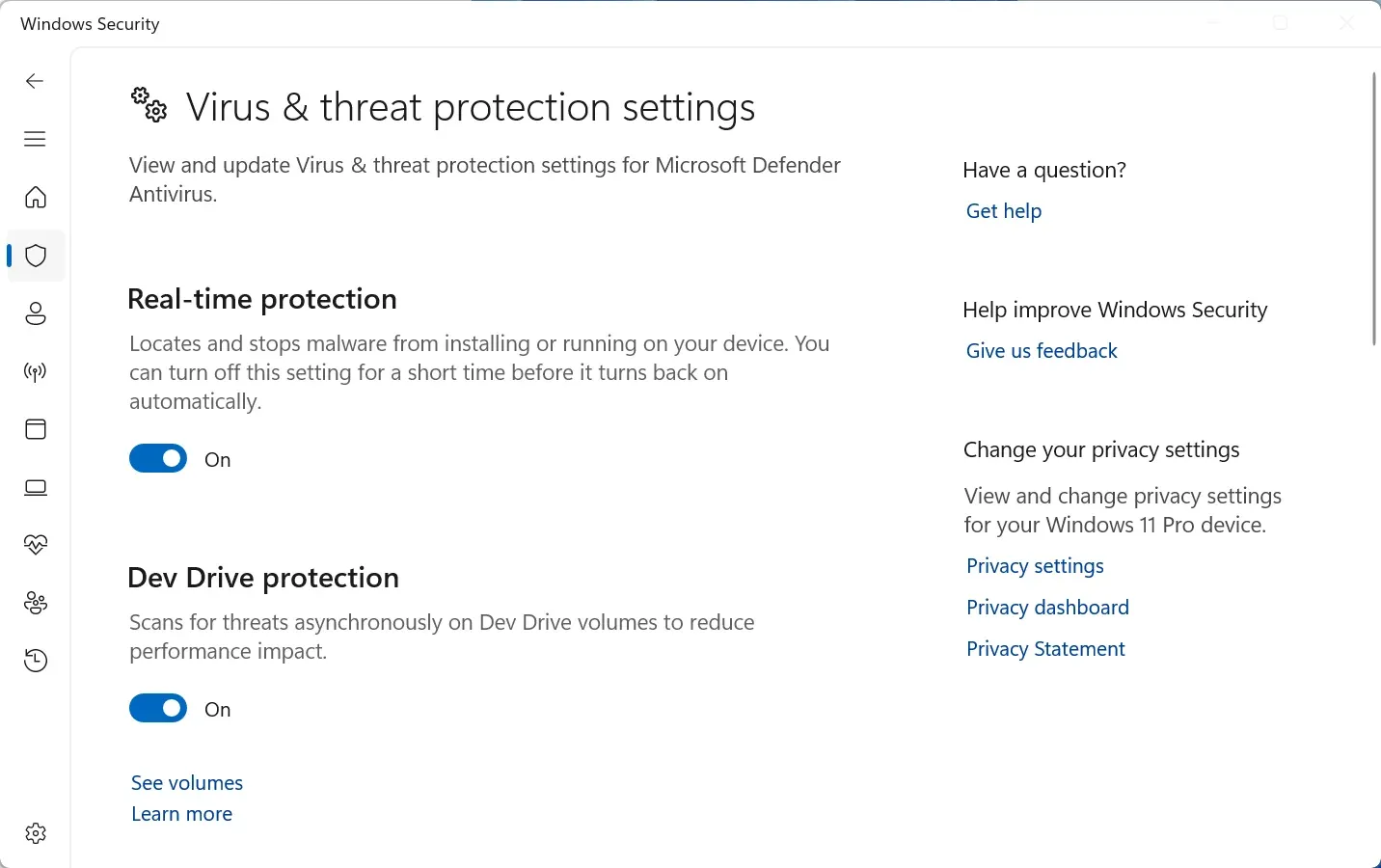
Configure Ransomware Protection:
This is critical and underutilized. Controlled folder access prevents unauthorized applications from modifying your important files.
- In Windows Security, go to Virus & threat protection
- Scroll down to Ransomware protection
- Click Manage ransomware protection
- Turn ON Controlled folder access
- Click Protected folders and verify your Documents, Pictures, Desktop folders are listed
- If you use other folders for important files, add them
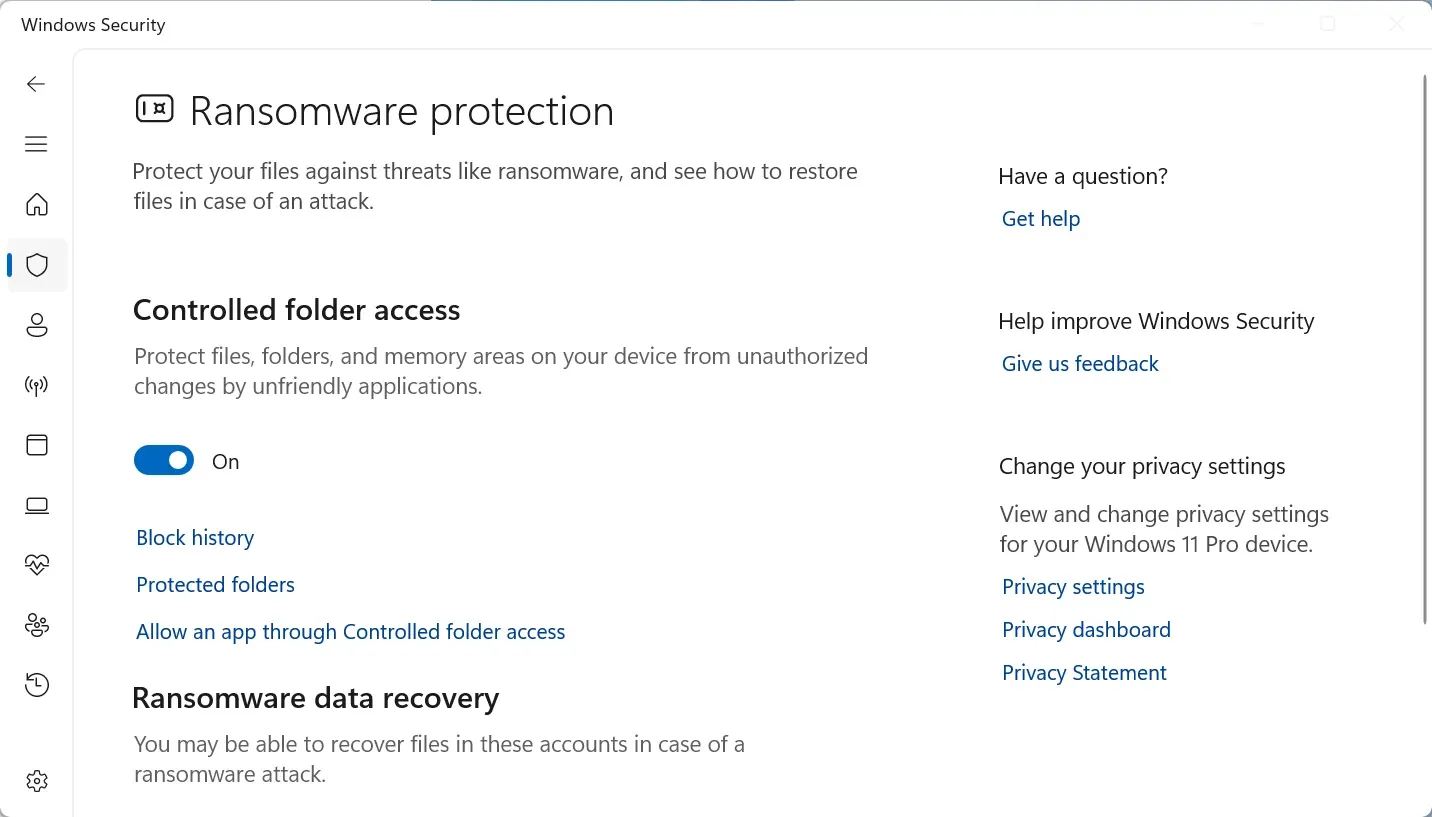
Important caveat: Some legitimate programs might get blocked initially. If this happens, click “Allow an app through Controlled folder access” and add the specific program. Yes, it’s an extra step, but it’s worth it—I’ve seen this feature stop ransomware cold.
Windows Firewall Configuration
The Windows Firewall blocks unauthorized network connections. Most people never touch it, which is actually fine—the defaults are good. But here’s what you should verify:
- Open Windows Security > Firewall & network protection
- Ensure firewall is ON for all three network types:
- Domain network (if you’re on a work network)
- Private network (home WiFi)
- Public network (coffee shop WiFi)
- Click Allow an app through firewall and review the list
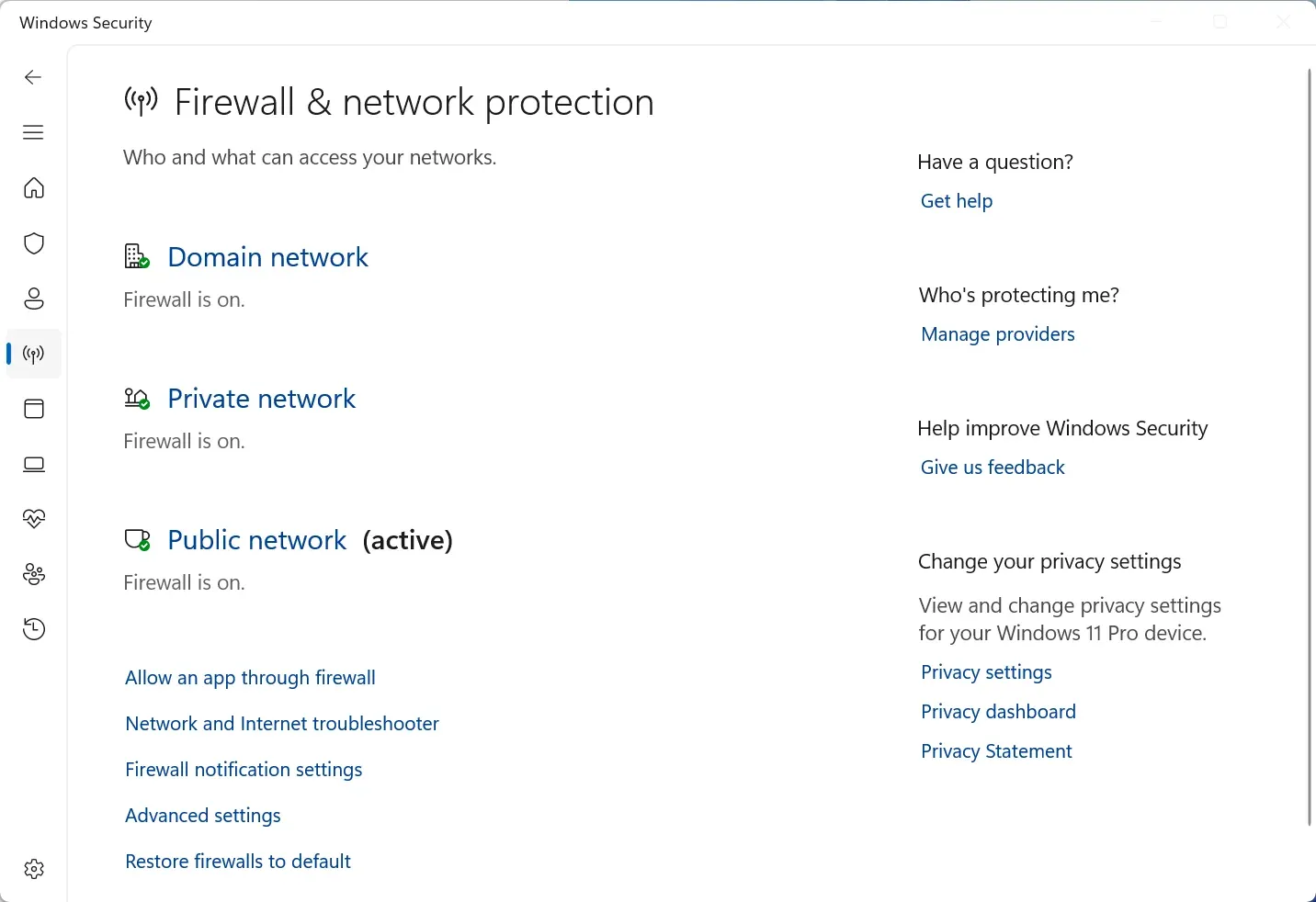
What to look for: Applications you don’t recognize or use. If you see something suspicious, research it before allowing network access.
When You Might Need Third-Party Antivirus
I’m not saying third-party antivirus is never worthwhile. Consider paid solutions if:
You want bundled features:
- VPN service included
- Password manager
- Parental controls
- Identity theft monitoring
- Dark web monitoring
- Premium support
You’re at higher risk:
- Business use (different threat model)
- You regularly download files from questionable sources
- You need centralized management across multiple PCs
- Compliance requirements for your industry
You want peace of mind: And that’s completely valid. If paying for antivirus helps you feel more secure, that psychological benefit has value.
My recommendation: Start with Microsoft Defender for 2-3 months. Make sure it’s properly configured. If you feel you need more features or protection, then consider third-party options. But don’t let marketing convince you that Microsoft Defender is inadequate—it’s not.
Layer 2: Windows Updates and Software Patching
I know. Windows Update can be incredibly annoying. It downloads gigabytes at inconvenient times, forces restarts when you’re in the middle of work, and occasionally breaks things.
But here’s what I tell every client: disabling Windows Update is one of the riskiest things you can do.
Why Updates Matter So Much
Think of software vulnerabilities like unlocked windows in your house. When Microsoft discovers a vulnerability, they release a patch to lock that window. But here’s the problem: the act of releasing a patch tells attackers exactly where the unlocked window is.
Within days (sometimes hours) of a patch being released, attackers create exploits targeting systems that haven’t updated yet. This is why “Patch Tuesday” (Microsoft’s monthly update cycle) is followed by “Exploit Wednesday”—attackers immediately target unpatched systems.
Real example from my consulting work: In 2024, a client’s business got hit with ransomware three weeks after Microsoft patched the vulnerability that was exploited. The company had disabled automatic updates to avoid disruptions. That “convenience” cost them over $50,000 in recovery, lost productivity, and—because they had to report the breach—damaged reputation.
Configuring Windows Update Properly
You can’t disable updates (on Windows 11 Home), but you can control when they happen:
- Go to Settings > Windows Update
- Click Advanced options
- Under Additional options, configure:
- Receive updates for other Microsoft products - Turn ON (updates Office, etc.)
- Get me up to date - Turn ON (accelerates important security updates)
- Set Active hours to match when you actually use your computer
- Consider scheduling restarts for overnight or specific times
For Windows 11 Pro users:
- You can defer feature updates (new Windows versions) by up to 365 days
- But never defer security updates—those address active threats
The risk here: Deferring security updates leaves your system vulnerable to exploits that attackers are actively using. Feature updates can wait; security patches cannot.
Beyond Windows: Third-Party Software Updates
Here’s something people overlook: your other software needs updates too. In fact, I’ve investigated breaches where the entry point was outdated versions of browsers, Adobe Reader, Java, media players, and compression tools.
The risk here: Attackers exploit outdated third-party software just as aggressively as Windows vulnerabilities. An unpatched browser is an open door.
My update strategy:
- Enable automatic updates for browsers (most do this by default now)
- Uninstall software you don’t use (fewer programs = smaller attack surface)
- Check for updates monthly for major applications
- Remove Adobe Flash Player if it’s still installed (discontinued and dangerous)
- Be suspicious of update prompts while browsing—real updates come from system notifications, not web popups
Layer 3: Identity Protection and Authentication
Let’s talk about passwords, because this is where I see the biggest gap between what people should do and what they actually do.
The Password Problem
Here’s the uncomfortable truth: the passwords most people use are terrible. Not because you’re careless, but because we’ve created an impossible situation. You’re supposed to use unique passwords for 100+ accounts, make them complex, change them regularly, and never write them down. This is unrealistic.
The risk here: When security advice is impossible to follow, people don’t follow it. Then they use “Password123” for everything and wonder why they get hacked.
The Practical Solution: Password Managers
Think of a password manager like a vault for your passwords. You remember one strong master password, and it generates and stores complex unique passwords for every account.
I always recommend password managers because:
- They generate truly random passwords (better than anything you’d create)
- They fill passwords automatically (more convenient than typing)
- They work across all your devices
- They can’t be phished (they won’t fill your bank password on a fake bank site)
- Many include dark web monitoring and breach alerts
Free options that work well:
- Bitwarden - Open source, excellent free tier
- Microsoft Authenticator - If you’re already in the Microsoft ecosystem
Paid options with more features:
- 1Password - User-friendly, family sharing
- LastPass - Feature-rich (though they’ve had security issues)
- Dashlane - Good VPN included
Getting started with password managers: The basic process is:
- Install the password manager
- Create a strong master password (use a passphrase like “correct-horse-battery-staple”)
- Start with your most important accounts (email, banking)
- Gradually add other accounts over time
- Enable two-factor authentication for the password manager itself
Yes, this takes effort upfront. But it’s a one-time investment that dramatically improves your security.
Two-Factor Authentication (2FA)
Here’s another layer: two-factor authentication. Think of it like a deadbolt on your door—even if someone steals your key (password), they still can’t get in without the second factor.
How 2FA works: After entering your password, you provide a second proof of identity:
- A code from an authenticator app
- A code texted to your phone (less secure but better than nothing)
- A physical security key
- Biometric verification (fingerprint, face)
Priority accounts for 2FA:
- Email (if this is compromised, attackers can reset all other passwords)
- Banking and financial accounts
- Work accounts
- Social media
- Password manager
- Cloud storage
My recommendation: Use authenticator apps (Microsoft Authenticator, Google Authenticator, Authy) rather than SMS when possible. SMS can be intercepted through SIM swapping attacks, though it’s still better than no 2FA.
Comprehensive two-factor authentication setup guide for major services covers Gmail, Microsoft accounts, banking apps, and more.
Windows Hello and Biometric Login
Windows 11 includes Windows Hello, which lets you log in with your face, fingerprint, or a PIN instead of typing a password.
Is this secure? Yes, actually. Here’s why:
- The biometric data stays on your device (not uploaded to Microsoft)
- It uses specialized hardware (TPM 2.0 chip required in Windows 11)
- PINs are device-specific (won’t work on another computer even if someone learns it)
- Faster than typing passwords (convenience increases security adoption)
To set up Windows Hello:
- Go to Settings > Accounts > Sign-in options
- Configure Facial recognition, Fingerprint recognition, or PIN depending on your hardware
- Keep password as backup method
The risk here is minimal, and the convenience is significant. I use it myself.
Layer 4: Network Security
Your internet connection is a pathway into your computer. Let’s make sure it’s secured properly.
Securing Your Home WiFi Network
I’m amazed how many people use default router passwords. Here’s the thing: those defaults are publicly available. Attackers literally have databases of every default router password by manufacturer.
The risk here: Default router passwords = unlocked front door. An attacker within WiFi range can access your router admin panel, change settings, and intercept all your traffic.
Essential WiFi security (30 minutes):
-
Change router admin password
- Log into router admin panel (usually 192.168.1.1 or 192.168.0.1)
- Find admin credentials (not the WiFi password—the router settings password)
- Change to a unique, strong password
-
Update router firmware
- Routers have software too, and it needs updates
- Check manufacturer website for latest firmware
- Some newer routers auto-update
-
Use WPA3 encryption (or WPA2 if WPA3 isn’t available)
- Never use WEP (ancient, completely broken)
- Find WiFi security settings in router admin panel
- Enable WPA3-Personal if supported, otherwise WPA2-Personal
-
Change default WiFi network name (SSID)
- Don’t use your name or address
- Doesn’t need to be random—just not identifying
- Example: “FBI Surveillance Van 7” (humor optional)
-
Disable WPS (WiFi Protected Setup)
- Convenient but vulnerable
- Find in router settings and turn off
-
Consider guest network for smart devices
- Separates IoT devices from your main computers
- If your smart fridge gets hacked, it can’t access your PC
Public WiFi: When You Need a VPN
I get asked about VPNs constantly. Here’s my honest take: for most home use, you don’t need one. But public WiFi is different.
Think of public WiFi like speaking loudly in a crowded room. Anyone nearby can eavesdrop on your conversation. A VPN creates a private tunnel that prevents eavesdropping.
To stay safe: Use a VPN when connected to coffee shop, airport, or hotel WiFi, especially when accessing banking or work systems. At home on your secured WiFi, HTTPS sites (the lock icon) provide sufficient encryption for most activities. VPNs don’t protect against malware—they only encrypt your connection.
VPN selection criteria:
- No-log policy (verify they’ve been audited)
- Kill switch (stops internet if VPN drops)
- Speed (check independent tests)
- Location (some countries have data retention laws)
- Price (free VPNs are usually harvesting your data instead)
Need a VPN recommendation now? If you’re traveling or frequently use public WiFi, consider a trusted VPN provider with independently audited no-log policies and strong encryption—avoid free VPNs that sell your data.
Layer 5: Data Protection and Backups
Let me be blunt: if you don’t have backups, you’re gambling with your data.
I’ve seen grown adults cry when they realize years of family photos are gone forever because ransomware encrypted everything and they had no backup. It’s heartbreaking, and it’s completely preventable.
The 3-2-1 Backup Strategy
This is the gold standard: 3 copies of your data, 2 different storage types, 1 copy offsite.
What this looks like practically: Original data on your PC, backup to external hard drive, backup to cloud storage.
The risk here: Ransomware encrypts connected drives. If your backup drive is always connected, it gets encrypted too. An offline backup (disconnected external drive) plus cloud backup protects against both ransomware and physical disasters.
To stay safe: Keep one backup disconnected (offline external drive rotated weekly) and one backup offsite (cloud). This protects against ransomware, hardware failure, and physical disasters.
Windows Backup and File History
Windows includes backup tools that most people never enable:
File History (for personal files):
- Connect external hard drive
- Go to Settings > System > Storage > Advanced storage settings > Backup options
- Click Add a drive and select your external drive
- Turn on Automatically back up my files
- Click More options to configure:
- How often to backup (I recommend hourly)
- How long to keep versions (space permitting, forever)
- Which folders to include
System Image Backup (for complete PC):
- Creates snapshot of entire system
- Useful for recovering from complete failure
- Requires significant storage space
- Find in Control Panel > Backup and Restore (Windows 7)
Cloud backup options:
- OneDrive (included with Microsoft 365)
- Google Drive
- Dropbox
- Backblaze (unlimited PC backup for ~$7/month)
My recommendation: Use File History for continuous backup to external drive, plus cloud backup for critical files. Test restoring files quarterly to verify backups work.
BitLocker Encryption
If your laptop gets stolen, do you want the thief accessing your files? BitLocker prevents this by encrypting your entire drive.
BitLocker availability:
- Included in Windows 11 Pro, Enterprise, Education
- Not available in Windows 11 Home (consider Device Encryption instead)
To enable BitLocker:
- Go to Settings > Privacy & security > Device encryption (Windows 11)
- Or search for BitLocker in Control Panel
- Turn on for your system drive
- CRITICAL: Save the recovery key somewhere safe (not on the encrypted drive)
- Print it and store physically
- Save to Microsoft account
- Save to file on different device
Warning: If you lose your BitLocker recovery key and forget your password, your data is permanently inaccessible. This is by design—encryption works.
Privacy Controls: Reducing Data Collection
Let’s address the elephant in the room: Windows 11 collects a lot of data about your usage. Some of this improves your experience, some funds Microsoft’s advertising business.
You can’t eliminate all data collection without breaking Windows functionality, but you can significantly reduce it.
Diagnostic Data and Telemetry
- Go to Settings > Privacy & security > Diagnostics & feedback
- Set Diagnostic data to Required diagnostic data only
- Required: Basic device info, settings
- Optional: Detailed usage, crash reports, browsing data
- Turn OFF these options:
- Improve inking and typing
- Tailored experiences
- View diagnostic data
- Click Delete under Delete diagnostic data
Trade-off: Some Windows features use diagnostic data to improve. But required data is sufficient for basic functionality.
App Permissions
Review app permissions regularly. Go to Settings > Privacy & security and restrict access for Location, Camera, Microphone for apps that don’t genuinely need them. My approach: start by denying everything, then grant permissions only when apps specifically request them for features you actually use.
Activity History and Advertising ID
Windows tracks activity history and uses an advertising ID for personalized ads. To minimize tracking: Go to Settings > Privacy & security > Activity history and turn OFF “Send my activity history to Microsoft,” then click Clear. Under General, turn OFF advertising ID and suggested content options. This doesn’t eliminate ads, just makes them generic instead of targeted.
Safe Browsing Practices
Here’s the thing: the best security software in the world can’t protect you if you click on malicious links or download infected files. Your behavior is the most important security layer.
Recognizing Phishing Attempts
Red flags that indicate phishing: sender address doesn’t match the company domain (hover over sender name to verify), generic greetings (“Dear customer”), urgent threats creating panic, requests for passwords or sensitive information via email, poor grammar and spelling, and suspicious links where the hover URL doesn’t match the displayed text.
To stay safe: Never click email links for banking or sensitive accounts. Type website addresses directly into your browser instead, or use bookmarks you’ve previously saved. When in doubt, call the company using the number from their official website—not a number provided in the email.
Browser Security Settings
Your browser needs protection too. Let me walk through securing Microsoft Edge (similar principles apply to Chrome and Firefox):
Microsoft Edge security:
- Go to Settings > Privacy, search, and services
- Tracking prevention: Set to Balanced (Strict can break some sites)
- Microsoft Defender SmartScreen: Turn ON
- Block potentially unwanted apps: Turn ON
- Under Security, ensure Microsoft Defender SmartScreen is ON
Extension safety: Browser extensions have full access to your browsing data. Be selective:
- Only install from official browser stores
- Check reviews and number of users
- Review what permissions they request
- Uninstall extensions you don’t actively use
- I recommend uBlock Origin for ad blocking (security benefit—blocks malicious ads)
HTTPS-Only Mode: Modern browsers can enforce HTTPS connections, preventing interception.
- Edge: Settings > Privacy > Security > “Automatically switch to HTTPS”
- Chrome: Settings > Privacy > Security > “Always use secure connections”
- Firefox: Settings > Privacy > HTTPS-Only Mode
Download Safety
Before downloading anything:
-
Verify it’s from the official source
- Google the software name
- Look for official website (usually first result, check URL carefully)
- Avoid download sites like download.com, softonic.com, cnet downloads
- These bundle adware and potentially unwanted programs
-
Check file reputation
- Right-click downloaded file > Properties > Digital Signatures tab
- Verify publisher matches expected company
- If no digital signature, be suspicious
-
Scan before opening
- Right-click file > Scan with Microsoft Defender
- Let it finish before opening
-
Research unfamiliar software
- Search “[software name] review” and “[software name] safe”
- Check Reddit, tech forums for user experiences
- Be wary of software that has no reviews
Red flags for malicious downloads:
- File extension doesn’t match claimed type (document.pdf.exe)
- Downloaded from email attachment
- Came from pop-up warning or ad
- Website required disabling antivirus to install
- Installation asks for admin rights without clear reason
Incident Response: What to Do If Compromised
Here’s the thing about security breaches: they’re not a matter of if, they’re a matter of when. Even with perfect security practices, you might click a convincing phishing link at 2am when you’re exhausted, or a zero-day exploit might slip past your defenses before patches are available.
I’ve guided dozens of clients through breach responses, and the pattern is always the same: panic first, then scrambling to figure out what to do. Let me give you the playbook now, so when (not if) something happens, you know exactly how to respond. Quick, systematic action minimizes damage—hesitation and confusion amplify it.
Immediate Actions
If you suspect active malware: Disconnect from internet immediately (unplug Ethernet or turn off WiFi) to prevent further data theft. Don’t restart yet—some malware activates on restart. Take phone photos of error messages, ransom notes, or strange popups to document the infection.
If you suspect account compromise: Change passwords immediately from a different, clean device. Enable 2FA if not already active. Review recent account activity (logins, sent emails, transactions), alert contacts if spam was sent from your account, and revoke access for unfamiliar connected apps and devices.
Malware Removal Process
Step 1: Boot into Safe Mode
Safe Mode loads Windows with minimal programs, preventing most malware from running.
- Go to Settings > System > Recovery
- Under Advanced startup, click Restart now
- Choose Troubleshoot > Advanced options > Startup Settings > Restart
- Press 4 or F4 for Safe Mode
Step 2: Run Microsoft Defender Offline Scan
This is a powerful tool that scans before Windows fully loads:
- In Safe Mode, open Windows Security
- Go to Virus & threat protection
- Under Current threats, click Scan options
- Select Microsoft Defender Offline scan
- Click Scan now (this will restart your PC)
Step 3: Use Additional Scanning Tools
If Defender finds nothing but you’re still suspicious:
- Malwarebytes (free version works for one-time scans)
- Kaspersky Virus Removal Tool (free, reputable)
- HitmanPro (good at finding rootkits)
Step 4: Check for Persistence Mechanisms
Malware often ensures it survives restarts:
- Check startup programs: Task Manager > Startup tab
- Review scheduled tasks: Task Scheduler (search in Start)
- Examine browser extensions: Remove anything unfamiliar
- Check hosts file: C:\Windows\System32\drivers\etc\hosts (should be mostly empty)
Step 5: Change All Passwords
After cleaning the infection:
- Change passwords for all important accounts
- Do this from a clean device initially (in case keylogger wasn’t removed)
- Start with email, banking, work accounts
When to Reinstall Windows
Sometimes it’s better to cut your losses:
Consider reinstalling if:
- Malware keeps reappearing after removal
- System is severely corrupted
- You suspect rootkit (very deep malware)
- Ransomware encrypted files
- You don’t trust the system is fully clean
How to reinstall while keeping files:
- Back up important files to external drive (scan them first)
- Go to Settings > System > Recovery
- Under Reset this PC, click Reset PC
- Choose Keep my files (or Remove everything for complete fresh start)
- Follow the wizard
Yes, this takes time. But it guarantees a clean system and is often faster than fighting persistent malware.
Advanced Security for High-Risk Users
The security measures covered so far protect 95% of Windows users from 95% of threats. But some of you need more. Maybe you handle sensitive client data, work in finance or healthcare, are a journalist or activist, or you’re just particularly paranoid (no judgment—security paranoia is often justified).
Here’s my honest assessment: these advanced measures add complexity and can break normal workflows if misconfigured. Only implement them if your threat model actually requires this level of protection. For most users, the earlier sections are more than sufficient. But if you’re in that 5% who needs defense-in-depth beyond the basics, here’s what to consider.
Windows Sandbox
Run untrusted programs in isolation without risking your main system. Think of it like a disposable virtual machine.
To enable Windows Sandbox:
- Go to Control Panel > Programs > Turn Windows features on or off
- Check Windows Sandbox
- Restart computer
- Launch from Start menu
Anything you do in Sandbox is completely isolated. When you close Sandbox, everything is deleted.
Use cases:
- Testing software before installing on main system
- Opening suspicious files
- Visiting questionable websites
Application Control and Hardware Security Keys
For businesses or high-security needs, Windows offers AppLocker (Pro/Enterprise) and Windows Defender Application Control to whitelist approved applications. These are complex and can break workflows if misconfigured—only for advanced users.
Hardware security keys (YubiKey, Titan Security Key) provide phishing-resistant 2FA that can’t be intercepted. They’re extremely secure but cost $25-60 and require physical access (necessitating backup methods).
Regular Security Maintenance
Security isn’t a one-time setup—it requires ongoing maintenance. Here’s my recommended schedule:
Weekly Tasks (5 minutes)
- Verify Windows Update ran successfully
- Check Windows Security for any threats or recommendations
- Glance at recently installed programs (uninstall anything unfamiliar)
Monthly Tasks (30 minutes)
- Run full Microsoft Defender scan
- Review startup programs (Task Manager > Startup)
- Check for software updates (browsers, common programs)
- Review browser extensions (remove unused)
- Verify backup ran successfully (check File History or cloud backup)
Quarterly Tasks (1 hour)
- Test restoring files from backup (ensure backups actually work)
- Review app permissions (Settings > Privacy & security)
- Change critical passwords (if not using password manager)
- Review and update recovery information (phone numbers, email addresses on accounts)
- Clean up old accounts you no longer use (reduces attack surface)
Yearly Tasks (2 hours)
- Comprehensive security review
- Update your backup strategy
- Review and update emergency contacts
- Consider security tools and whether your needs have changed
- Review this guide for any updates (I’ll keep it current)
Building a Sustainable Security Routine
Here’s what I’ve learned from a decade of consulting: perfect security that you don’t maintain is worse than good security that you stick with consistently.
Start with the essential layers:
- Enable and configure Microsoft Defender (30 minutes today)
- Turn on automatic Windows Updates (5 minutes today)
- Set up password manager (1 hour this week)
- Enable 2FA on critical accounts (2 hours this month)
- Configure automatic backups (1 hour this week)
Those five things will protect you from 95% of threats you’ll actually encounter.
Then gradually add:
- Privacy controls
- Advanced authentication
- Additional tools as needed for your specific risk level
Don’t try to implement everything at once. You’ll get overwhelmed and give up. Build sustainable habits incrementally.
Frequently Asked Questions
Do I really need third-party antivirus software in 2025?
For most users, honestly, no. Microsoft Defender has evolved significantly and now provides excellent protection that matches or exceeds many paid antivirus solutions. In independent testing (AV-TEST, AV-Comparatives), Defender consistently scores in the top tier for malware detection.
The risk here is that antivirus marketing creates fear that Windows Security isn’t enough—but it absolutely is for 95% of users. Consider third-party antivirus only if you need bundled features like VPN, password manager, or parental controls, or if you’re in a high-risk environment requiring additional protection layers.
Is Windows Defender actually good enough for serious protection?
Yes, and I say this after 10+ years in cybersecurity. Modern Microsoft Defender includes real-time protection, cloud-delivered threat intelligence, ransomware protection with controlled folder access, exploit protection against zero-days, and integrated firewall.
To stay safe, enable all protection features (especially Tamper Protection and Controlled folder access), keep Windows updated, and combine it with safe browsing practices. The combination of properly configured Defender plus user awareness provides excellent security without third-party software costs.
Should I use a VPN at home on my secure WiFi network?
For most home use on your own WiFi, you don’t need a VPN. If you’ve secured your router properly (WPA3/WPA2 encryption, strong password, firmware updated), your home network is already encrypted.
VPNs are critical for public WiFi (coffee shops, airports, hotels) where anyone on the network can potentially intercept traffic. At home, VPNs only help if you want to hide browsing from your ISP, access geo-restricted content, or add an extra privacy layer. The risk here is minimal for home use—focus your security efforts on stronger passwords, 2FA, and backups instead.
How can I tell if my computer has been infected with malware?
Warning signs include: unusual slowness or high CPU usage when idle (check Task Manager), programs launching automatically that you didn’t install, browser homepage or search engine changed without your input, excessive pop-up ads appearing even outside the browser, unfamiliar programs in your installed apps list, antivirus disabled and won’t turn back on, and frequent crashes or error messages. For systematic approaches to diagnosing crashes and errors, see our Windows troubleshooting guide.
To stay safe, run a full Microsoft Defender scan, use second-opinion scanner like Malwarebytes free, boot into Safe Mode and scan again, check Task Manager > Startup tab for unfamiliar programs, and review browser extensions for anything suspicious. If malware persists after removal attempts, consider a clean Windows reinstall.
What's the best way to create strong passwords I can actually remember?
Use a password manager—full stop. The old advice about creating memorable passwords doesn’t scale when you need unique passwords for 50+ accounts.
Password managers like Bitwarden (free), 1Password (paid), or Microsoft Authenticator generate truly random 16+ character passwords, store them securely, fill them automatically, work across all devices, and can’t be phished (they won’t fill your bank password on a fake site). The only password you need to remember is your master password—make it a long passphrase like “correct-horse-battery-staple” (4+ random words).
To stay safe, never reuse passwords across accounts, enable 2FA on your password manager itself, and start with your most critical accounts (email, banking) then gradually migrate others.
Should I turn off Windows diagnostic data collection for better privacy?
Set it to “Required diagnostic data only” instead of completely off. Required data includes basic device information, settings, and capabilities—necessary for Windows to function properly and receive security updates. Optional data includes detailed usage patterns, crash reports, and browsing data that Microsoft uses for product improvement and advertising.
The trade-off is reasonable: you keep full Windows functionality while significantly reducing data collection. To stay safe, also disable “Improve inking and typing,” “Tailored experiences,” and regularly delete diagnostic data via Settings > Privacy & security > Diagnostics & feedback.
How often should I back up my important files?
For critical files (family photos, work documents, financial records), use continuous or daily automated backups. Windows File History can back up hourly to an external drive—set it and forget it. Cloud backup services like OneDrive, Google Drive, or Backblaze sync continuously in the background.
Follow the 3-2-1 rule: 3 copies of data, 2 different storage types (external drive + cloud), 1 copy offsite. The risk here is catastrophic: ransomware can encrypt everything including connected backup drives. An offline backup (disconnected external drive you rotate weekly) plus cloud backup protects against both ransomware and physical disasters (fire, theft, hardware failure).
Is public WiFi really dangerous, or is that exaggerated?
Public WiFi is legitimately risky if you’re accessing sensitive accounts without protection. Think of it like speaking loudly in a crowded room—anyone nearby with basic tools can eavesdrop on unencrypted traffic. Modern HTTPS (the lock icon) encrypts most web traffic, which helps significantly.
However, attackers on public WiFi can still perform man-in-the-middle attacks, create fake “Evil Twin” networks that look legitimate, or intercept unencrypted traffic. To stay safe on public WiFi: use a VPN to encrypt all traffic, verify you’re connecting to the legitimate network name, avoid accessing banking or sensitive accounts, and never enter passwords on HTTP sites (only HTTPS). At minimum, stick to HTTPS sites and avoid anything sensitive.
Do I need to change my passwords regularly, or is that outdated advice?
Password rotation is mostly outdated advice that created more problems than it solved. Current NIST guidelines (National Institute of Standards and Technology) say don’t force regular password changes unless there’s evidence of compromise. Why? Forced changes led people to create weaker passwords (Password1, Password2, Password3) or make minimal changes (adding ”!” at the end).
To stay safe instead: use strong unique passwords for every account (via password manager), enable 2FA on critical accounts, monitor for breaches (many password managers include dark web monitoring), change passwords immediately if a service announces a breach, and never reuse passwords across accounts. One strong password with 2FA that never changes is infinitely better than weak passwords changed monthly.
How do I know if an email is actually a phishing attempt?
Check these red flags: sender email address doesn’t match the company domain (hover over sender name to see real address—legitimate PayPal uses @paypal.com, not @paypa1-security.com), generic greeting (“Dear Customer” instead of your name), urgent threats creating panic (“Account suspended in 24 hours!”), requests for passwords or sensitive information via email (legitimate companies never ask), poor grammar and spelling errors, and suspicious links (hover without clicking to see real URL—link text may say paypal.com but actually goes to phishing site).
To stay safe: never click links in emails for banking, payment, or sensitive accounts, type website addresses directly into browser instead, use bookmarks for frequent sites, and when in doubt call the company using the number from their official website (not a number in the email). If an email creates urgency and panic, that’s intentional—phishers want you to act without thinking.
Can I safely disable Windows Update to prevent it from interrupting my work?
No, and here’s why this is so risky: when Microsoft releases security patches, they’re simultaneously telling attackers exactly where vulnerabilities exist. Within hours of “Patch Tuesday” (Microsoft’s monthly update cycle), attackers create exploits targeting unpatched systems. I’ve seen businesses suffer ransomware attacks just weeks after Microsoft patched the exact vulnerability that was exploited—they’d disabled updates to avoid disruptions.
To stay safe while minimizing interruptions: keep automatic updates enabled, set Active Hours in Windows Update settings (prevents restarts during work hours), schedule restarts for overnight or specific times, enable “Get me up to date” for accelerated security updates, and never defer security updates (feature updates can wait, security patches cannot). The inconvenience of occasional restarts is nothing compared to the catastrophic cost of a preventable breach.
Conclusion: Practical Windows Security Without Paranoia
I’ve thrown a lot at you in this comprehensive Windows security guide. Let me distill it to what actually matters:
The fundamentals that prevent most problems:
- Keep Windows and software updated
- Use Microsoft Defender properly configured
- Use strong, unique passwords (via password manager)
- Enable two-factor authentication on important accounts
- Maintain backups (3-2-1 strategy)
- Think before clicking links or downloading files
That’s it. Yes, there are more advanced security measures in this guide. But if you do those six things consistently, you’re more secure than 90% of Windows users.
Windows security doesn’t have to consume your life or make you paranoid. It’s about building sustainable habits that protect your PC without constant worry.
What to do next:
- Spend 30 minutes today configuring Microsoft Defender properly
- This week, set up File History or cloud backup
- This month, implement a password manager
- This quarter, enable 2FA on your email and banking
I’ll be publishing detailed guides on each of these topics as part of our security series. Bookmark this page and check back for updates.
Found this guide helpful? Share it with someone who needs better Windows security—you might save them from a ransomware attack or data breach. Security is one area where an ounce of prevention truly is worth a pound of cure.
Dive deeper into Windows security:
- Complete Microsoft Defender Setup Guide - Detailed walkthrough of protection configuration
- Malware Identification and Removal Guide - Step-by-step troubleshooting for infected systems
- Safe Browsing Practices Guide - Recognizing threats online before they compromise your PC
- Two-Factor Authentication Setup Guide - Adding extra security to your critical accounts
- Privacy Settings in Windows 11 Guide - Comprehensive privacy configuration
Stay safe out there. And remember: if something seems suspicious, trust your instincts. That gut feeling has probably saved you more times than you realize.
If you have questions about anything in this guide, I’m here to help. Security can seem overwhelming, but we’ll break it down together into manageable steps.
